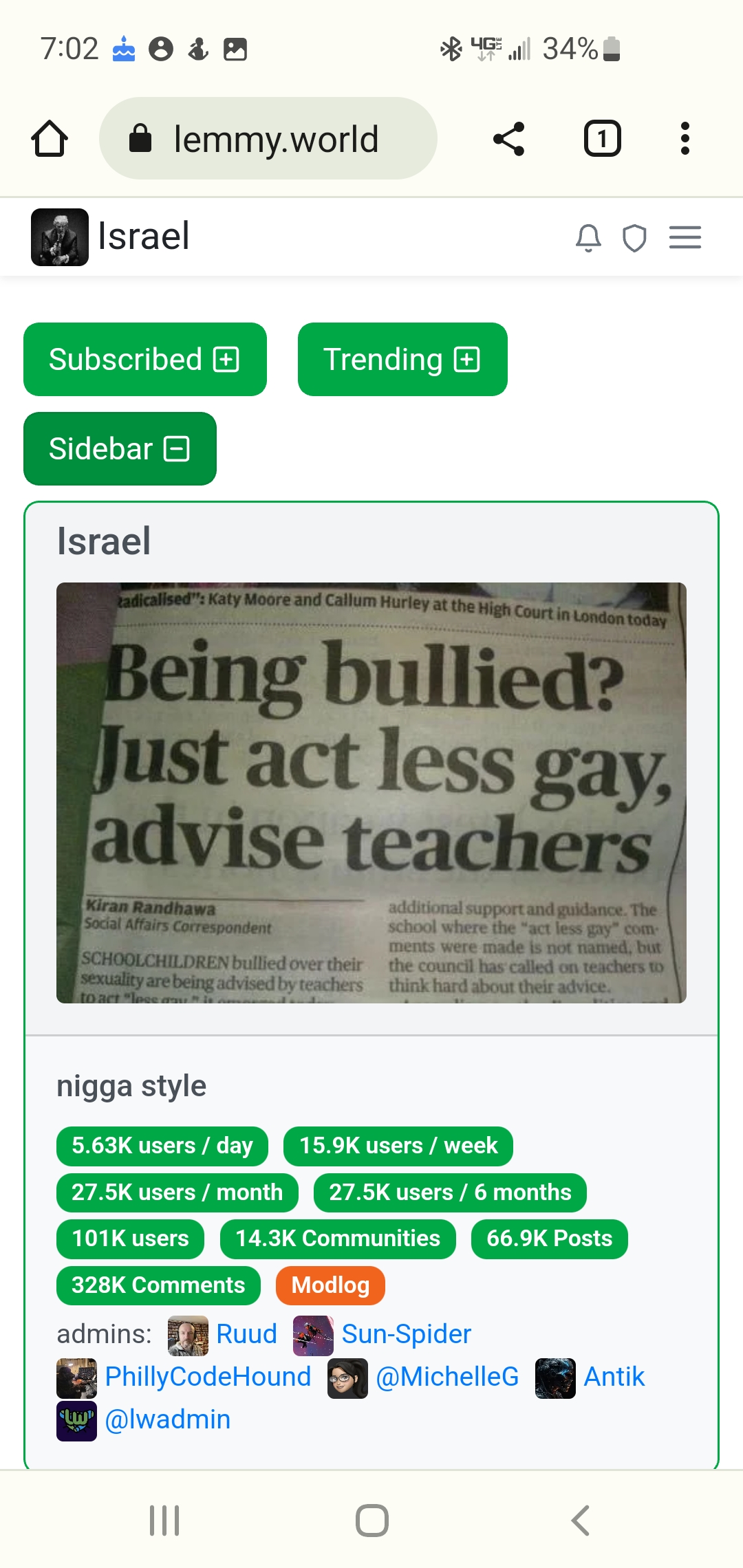
When logging into lemmy.world the banner now says “Israel - ni**a style” (full word unredacted) and it starts linking to lemon party and a bunch of other NSFW sites.
Reddit operatives are trying to sabotage Lemmy! That’s my conspiracy anyway.
Lol. A wild one
Correct. I do not believe it.
Spez hired Pinkertons to sabotage Lemmy!
Pinkerton scum.
I kinda would believe meta doing it, tho. Only in purely conspiracy theorist levels, but it kinda is a possibility…
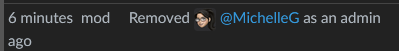
Yea. Looks like they are working on it:
EDIT: Looks like things are starting to resolve.
EDIT 2: MichelleG account admin was restored and she posted and update but shortly after the changes happened again. Her account is likely still compromised with someone else accessing things via it.
EDIT 3: lemmy.world back online. MichelleG has again been removed as admin. Most things appear to have been cleaned up. Blocked instances still need to be fixed however.
Mods account got compromised or went rogue?
Worse. Admin account. The MichelleG account is an admin and it appears that it was compromised and is what is causing all the problems. It looks like they have removed it from admin so things wont get worse but they will likely take a bit to find and repair all the stupid little changes that were made.
The sidebar was changed.
Obviously some javascript was installed to the frontpage that makes us redirect to lemon party (NSFW) ponographic site.
Logo on top of the screen has changed, anti-Israel has been plastered all over the place.
This is not inspiring confidence in their security. 2FA was off or was somehow circumvented.
If a JWT token was stolen 2FA wouldn’t matter.
Encountered that too. Would it be recommended to change passwords and logins though?
We’ll see what they say but never a bad idea. Hopefully logins are encrypted and salted but I don’t use this username or password anywhere else.
That’s the ideal situation. It’s been restored and I’m yet to see anything related to ‘login credentials being compromised’ or an advice to change them but as you said, it’s not a bad idea. Safety first
The tasteless redirect & site-title-change seems to have gone away. The admins have retaken the site, now just cleaning up the junior edgelord’s mess.
Is there a discord or something people are in?
Not that I am aware of at least.
Yeah the admins have said they’re hands off and all but one person managing the world community isn’t active since ruud doesn’t check his notifications.
Somewhat concerning tbh
Even an admin account should probably not be able to inject Javascript. Something a little sloppy going on there.
Kind of annoying that someone can just brick the entire server like this. I keep getting redirected just trying to get to the main page
Apps are able to deal with it
nah. they don’t. mine didn’t loaded anything anymore and couldn’t do anything anymore. can’t even open my messages anymore.
Yeah I redirect to lemon party every so often.
Damn that’s a nostalgia trip. Haven’t seen lemon party in a long time. Early internet was full of links to it.
Dear god Lemon
Ain’t no party like a Liz lemon party
'cause a Liz Lemon party is mandatory!
(That was one of my favorite lines. Loved that show.)
Don’t forget “Can’t have a Lemon party without old Dick!” (Her dad) 🤣
still having this problem, at least we are aware that this could happen down the road as an early warning
Looks like they changed the name to Israel lol
Good job on the cleanup.
I’m not seeing any issues anymore, at least from my end.
Just got another redirect, it’s definitely still happening.
Based on the Github / Rudd’s new post, it looks like there was an “Evil Post” that contained a Markdown-to-Javascript escape and actually allowed the hacker to run Javascript in our web-browsers. Something to do with custom emojis?
So the problem was multi-fold.
-
The hacker created the “Evil Post”, which constantly was stealing people’s cookies. Anyone who viewed the evil post in a web browser (Chrome/Firefox/Edge) allowed the hacker to have access to their account (and anything you can do in the web browsers).
-
The hacker waited until an admin viewed the post. Then took control of the administrator’s account, and likely a few other people’s accounts as well. DMs containing the evil-Javascript post were sent to various moderators.
-
Hacker used the account access to just troll us.
Fixing #3 doesn’t fix #2 or #1. So eventually, when #3 was fixed, the hacker just grabbed the admin-account and made everything back to the way it was.
The problem wouldn’t be fixed permanently until #3, #2, and #1 were all fixed. Which they seem to be fixed now. But this “evil post” is going around the Federation. Other Lemmy-instances may have the post cached, and the users on those lemmies will likely have their JWT cookie also stolen (allowing the hacker to take over people’s accounts those instances in a similar manner)
-
Yes. You seeing this
Damn, I can’t tell if edgy teenager or someone more malicious posing as one
The former, he mad because people are fed up with the shit of people like him on reddit
Surely 2FA must have been off for that to happen, if so that doesn’t inspire confidence…
Personally I don’t use 2fa even though I want to. I use bitwarden for everything and I have no way to set up 2fa inside bitwarden. I can set it up through authy but prefer not to.
I have 2fa working in bitwarden for some places. I do pay for a subscription though, not sure if that makes a difference
I use it everywhere but Lemmy because for whatever reason the link to set it up won’t give me a manual code or QR code it forces me to open it in an ap like Authy or Google Auth. Those are just the ones I have installed I’m sure others would work as well.
Its $10 a year man come on https://bitwarden.com/pricing/
Narrator voiceover: In today’s lesson @ExcursionInversion learns that the world is not the USA and vice versa.
What’s the price in RMB and do they take payment by WeChat Wallet or Alipay?
Oh, what’s that? You don’t know what any of that even is?
Perhaps you’re not in a position to say “come on” then. Given that the site doesn’t even have i18n for the overwhelming majority of world languages, I’m pretty confident in guessing they don’t support a whole lot of payment options accessible to the bulk of the world as well.
In case you are actually interested. https://bitwarden.com/help/billing-faqs/#q-what-payment-options-do-you-accept-for-customers-outside-the-united-states
So they don’t accept payment in RMB over AliPay or Wechat is what you’re saying?
What. A. Surprise.
Credit cards are incredibly unpopular here: I’ve literally not seen one in use that wasn’t by a tourist in a tourist-oriented shop in 20 years. “Debit card” is so vague it’s almost charming. Paypal isn’t easily available as an option in most of the world. (I, for example, to use Paypal, would have to jump through incredibly time-consuming and expensive hoops to use its ‘letter of credit’ option.) I don’t know what “ACH” is, but I can pretty much guarantee that I can’t pay from my bank account given the currency export restrictions, etc. etc. etc. etc.
So again: today’s lesson was “the world is not the USA and vice versa”.
Yea for your average user I can get that, but this was an admin account. Sounds like 2FA was already compromised so will be interesting to understand how that happened in the first place.