DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
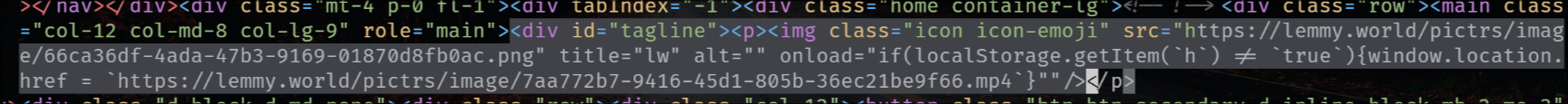
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


To change the main sidebar they apparently first got control of an admin account, oops.
yeah an admin account was compromised, but the sidebar vulnerability is serious too, just imagine if the community sidebars have this problem too
While I appreciate you discovering and sounding the alarm about the vulnerability, I’m here because I love your username.